If you want to experiment a little with PKI (public key infrastructure), SmartCard technology and other securty-related topics, you can create a certificate for yourself for free. Here is how it works.
Installing XCA
XCA is a great software to manage everything related to certificates. Just download and install it.
It’s a good idea to install all modules.
Creating a Certificate Authority
We want to do things right, so the 1st thing we need is a certificate authority. The authority can issue and revoke certificates. As soon as it comes to advanced tasks, we’ll need it anyway. Creation is easy, so let’s go.
Start XCA
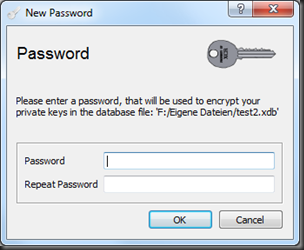
Create a new Database
This is going to store all your valuable certificates, so give it a good password. I recommend to store the database file on an external flash drive and to keep it in a safe place as long as you don’t use it.
Press “New Certificate”
Select “[default] CA” as template and press “apply all”. This will fill all the advanced fields to create a CA (certificate authority) certificate.
Enter a meaningful name for “internal name”. This name is used only within the XCA application, so it’s just for you.
You should definily fill the commonName. This is showen as the certificate name everywhere you’ll be using it. You can name it “yourdomainname.com CA” for example.
Every certificate needs a key pair, so please generate one pressing “Generate a new key”
Select “RSA” and 2048 bit as keysize. Those settings are recommended if you want to load your certificate to a SmartCard later on.
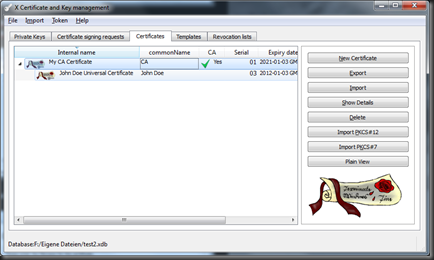
Done! Now we have the CA created as you can see.
Create Personal Certificate
Usually we’d now create a bunch of certificates. One for email encytion, one for VPN, one for Windows Logon, one for …
This is useful since they are independant and for example you can revoke them individually if something should go wrong. Anyway, we’ll do the bad practice and create just one “universal” certificate being capable of everything.
Press “New Certificate” again.
This time, we don’t apply a template but switch to the Subject Tab right away. Enter the internal name and common Name. This time, you should name it after your First and Lastname to indicate, that this is your personal certificate. Also, generate a new RSA, 2048bit key for this certificate.
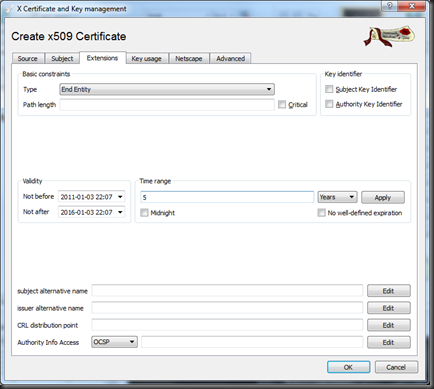
In the “Extensions” Tab, you might want to extend the validity to 5 years. Expiration increases security in case you lose your key or it’s compromised. Then press OK
In the “key usage” tab, select all entries in both columns. This ensures that you’ll have no restriction. Again: this is bad practice. If you want to do it right, create one certificate per application and assign rescricted key usage permissions.
Press OK
Done! You can see in the certificate chain, that your personal certificate.
Exporting your personal certificate
Now select your personal certificate and press “Export”
The correct exort format is “PKCS #12 with Certificate chain”. This format includes
- your personal key pair (public and private)
- your personal certificate
- all parent certificates up until the root CA certificate
To protect your keys, the file is encrypted by a password. Whenever you want to use your certificate, you need to enter the password.
Keep the exported file in a safe place. Even if it’s password protected, make sure noone else but you can access it. The safest storage is on a SmartCard.
Exporting the CA certificate
For advanced applications, you’ll need to have the CA certificate. That’s why you should export it. Select it and press “Export”
It’s very important to understand that we don’t export the CA’s private key now. It remains within your XCA database only and can only be used for certificate creation. Our export contains the public key and the certificate only. This is enough for other applications to verify, that our personal key was signed by the CA. That’s all they need.
Select the export format PEM and press OK
Summary
You created
- a XDB Database that should be stored in a safe place, offline.
- a P12 Certificate file that contains your password-protected secret key
- a CA certificate file that does not contain any secrets














1 Kommentar:
Kommentar veröffentlichen